Bacula FD Plugin API
To write a Bacula plugin, you create a dynamic shared object program (or dll on Win32) with a particular name and two exported entry points, place it in the Plugins Directory, which is defined in the bacula-fd.conf file in the Client resource, and when the FD starts, it will load all the plugins that end with -fd.so (or -fd.dll on Win32) found in that directory.
Normal vs Command vs Options Plugins
In general, there are three ways that plugins are called. The first way, is when a particular event is detected in Bacula, it will transfer control to each plugin that is loaded in turn informing the plugin of the event. This is very similar to how a RunScript works, and the events are very similar. Once the plugin gets control, it can interact with Bacula by getting and setting Bacula variables. In this way, it behaves much like a RunScript. Currently very few Bacula variables are defined, but they will be implemented as the need arises, and it is very extensible.We plan to have plugins register to receive events that they normally would not receive, such as an event for each file examined for backup or restore. This feature is not yet implemented.
The second type of plugin, which is more useful and fully implemented in the current version is what we call a command plugin. As with all plugins, it gets notified of important events as noted above (details described below), but in addition, this kind of plugin can accept a command line, which is a:
Plugin = <command-string>
directive that is placed in the Include section of a FileSet and is very similar to the "File = " directive. When this Plugin directive is encountered by Bacula during backup, it passes the "command" part of the Plugin directive only to the plugin that is explicitly named in the first field of that command string. This allows that plugin to backup any file or files on the system that it wants. It can even create "virtual files" in the catalog that contain data to be restored but do not necessarily correspond to actual files on the filesystem.
The important features of the command plugin entry points are:
- It is triggered by a "Plugin =" directive in the FileSet
- Only a single plugin is called that is named on the "Plugin =" directive.
- The full command string after the "Plugin =" is passed to the plugin so that it can be told what to backup/restore.
The third type of plugin is the Options Plugin, this kind of plugin is useful to implement some custom filter on data. For example, you can implement a compression algorithm in a very simple way. Bacula will call this plugin for each file that is selected in a FileSet (according to Wild/Regex/Exclude/Include rules). As with all plugins, it gets notified of important events as noted above (details described below), but in addition, this kind of plugin can be placed in a Options group, which is a:
FileSet {
Name = TestFS
Include {
Options {
Compression = GZIP1
Signature = MD5
Wild = "*.txt"
Plugin = <command-string>
}
File = /
}
}
Loading Plugins
Once the File daemon loads the plugins, it asks the OS for the two entry points (loadPlugin and unloadPlugin) then calls the loadPlugin entry point (see below).Bacula passes information to the plugin through this call and it gets back information that it needs to use the plugin. Later, Bacula will call particular functions that are defined by the loadPlugin interface.
When Bacula is finished with the plugin (when Bacula is going to exit), it will call the unloadPlugin entry point.
The two entry points are:
bRC loadPlugin(bInfo *lbinfo, bFuncs *lbfuncs, pInfo **pinfo, pFuncs **pfuncs) and bRC unloadPlugin()
both these external entry points to the shared object are defined as C entry points to avoid name mangling complications with C++. However, the shared object can actually be written in any language (preferably C or C++) providing that it follows C language calling conventions.
The definitions for bRC and the arguments are src/filed/fd-plugins.h and so this header file needs to be included in your plugin. It along with src/lib/plugins.h define basically the whole plugin interface. Within this header file, it includes the following files:
#include <sys/types.h> #include "config.h" #include "bc_types.h" #include "lib/plugins.h" #include <sys/stat.h>
Aside from the bc_types.h and confit.h headers, the plugin definition uses the minimum code from Bacula. The bc_types.h file is required to ensure that the data type definitions in arguments correspond to the Bacula core code.
The return codes are defined as:
typedef enum {
bRC_OK = 0, /* OK */
bRC_Stop = 1, /* Stop calling other plugins */
bRC_Error = 2, /* Some kind of error */
bRC_More = 3, /* More files to backup */
bRC_Term = 4, /* Unload me */
bRC_Seen = 5, /* Return code from checkFiles */
bRC_Core = 6, /* Let Bacula core handles this file */
bRC_Skip = 7, /* Skip the proposed file */
} bRC;
At a future point in time, we hope to make the Bacula libbac.a into a shared object so that the plugin can use much more of Bacula's infrastructure, but for this first cut, we have tried to minimize the dependence on Bacula.
loadPlugin
As previously mentioned, the loadPlugin entry point in the plugin is called immediately after Bacula loads the plugin when the File daemon itself is first starting. This entry point is only called once during the execution of the File daemon. In calling the plugin, the first two arguments are information from Bacula that is passed to the plugin, and the last two arguments are information about the plugin that the plugin must return to Bacula. The call is:bRC loadPlugin(bInfo *lbinfo, bFuncs *lbfuncs, pInfo **pinfo, pFuncs **pfuncs)
and the arguments are:
- lbinfo
- This is information about Bacula in general. Currently, the only value defined in the bInfo structure is the version, which is the Bacula plugin interface version, currently defined as 1. The size is set to the byte size of the structure. The exact definition of the bInfo structure as of this writing is:
typedef struct s_baculaInfo { uint32_t size; uint32_t version; } bInfo; - lbfuncs
- The bFuncs structure defines the callback entry points within Bacula that the plugin can use register events, get Bacula values, set Bacula values, and send messages to the Job output or debug output.
The exact definition as of this writing is:
typedef struct s_baculaFuncs { uint32_t size; uint32_t version; bRC (*registerBaculaEvents)(bpContext *ctx, ...); bRC (*getBaculaValue)(bpContext *ctx, bVariable var, void *value); bRC (*setBaculaValue)(bpContext *ctx, bVariable var, void *value); bRC (*JobMessage)(bpContext *ctx, const char *file, int line, int type, utime_t mtime, const char *fmt, ...); bRC (*DebugMessage)(bpContext *ctx, const char *file, int line, int level, const char *fmt, ...); void *(*baculaMalloc)(bpContext *ctx, const char *file, int line, size_t size); void (*baculaFree)(bpContext *ctx, const char *file, int line, void *mem); } bFuncs;We will discuss these entry points and how to use them a bit later when describing the plugin code.
- pInfo
- When the loadPlugin entry point is called, the plugin must initialize an information structure about the plugin and return a pointer to this structure to Bacula.
The exact definition as of this writing is:
typedef struct s_pluginInfo { uint32_t size; uint32_t version; const char *plugin_magic; const char *plugin_license; const char *plugin_author; const char *plugin_date; const char *plugin_version; const char *plugin_description; } pInfo;Where:
- version
- is the current Bacula defined plugin interface version, currently set to 1. If the interface version differs from the current version of Bacula, the plugin will not be run (not yet implemented).
- plugin_magic
- is a pointer to the text string "*FDPluginData*", a sort of sanity check. If this value is not specified, the plugin will not be run (not yet implemented).
- plugin_license
- is a pointer to a text string that describes the plugin license. Bacula will only accept compatible licenses (not yet implemented).
- plugin_author
- is a pointer to the text name of the author of the program. This string can be anything but is generally the author's name.
- plugin_date
- is the pointer text string containing the date of the plugin. This string can be anything but is generally some human readable form of the date.
- plugin_version
- is a pointer to a text string containing the version of the plugin. The contents are determined by the plugin writer.
- plugin_description
- is a pointer to a string describing what the plugin does. The contents are determined by the plugin writer.
The pInfo structure must be defined in static memory because Bacula does not copy it and may refer to the values at any time while the plugin is loaded. All values must be supplied or the plugin will not run (not yet implemented). All text strings must be either ASCII or UTF-8 strings that are terminated with a zero byte.
- pFuncs
- When the loadPlugin entry point is called, the plugin must initialize an entry point structure about the plugin and return a pointer to this structure to Bacula. This structure contains pointer to each of the entry points that the plugin must provide for Bacula. When Bacula is actually running the plugin, it will call the defined entry points at particular times. All entry points must be defined.
The pFuncs structure must be defined in static memory because Bacula does not copy it and may refer to the values at any time while the plugin is loaded.
The exact definition as of this writing is:
typedef struct s_pluginFuncs { uint32_t size; uint32_t version; bRC (*newPlugin)(bpContext *ctx); bRC (*freePlugin)(bpContext *ctx); bRC (*getPluginValue)(bpContext *ctx, pVariable var, void *value); bRC (*setPluginValue)(bpContext *ctx, pVariable var, void *value); bRC (*handlePluginEvent)(bpContext *ctx, bEvent *event, void *value); bRC (*startBackupFile)(bpContext *ctx, struct save_pkt *sp); bRC (*endBackupFile)(bpContext *ctx); bRC (*startRestoreFile)(bpContext *ctx, const char *cmd); bRC (*endRestoreFile)(bpContext *ctx); bRC (*pluginIO)(bpContext *ctx, struct io_pkt *io); bRC (*createFile)(bpContext *ctx, struct restore_pkt *rp); bRC (*setFileAttributes)(bpContext *ctx, struct restore_pkt *rp); bRC (*checkFile)(bpContext *ctx, char *fname); } pFuncs;The details of the entry points will be presented in separate sections below.
Where:
- size
- is the byte size of the structure.
- version
- is the plugin interface version currently set to 3.
Sample code for loadPlugin:
bfuncs = lbfuncs; /* set Bacula funct pointers */ binfo = lbinfo; *pinfo = &pluginInfo; /* return pointer to our info */ *pfuncs = &pluginFuncs; /* return pointer to our functions */ return bRC_OK;
where pluginInfo and pluginFuncs are statically defined structures. See bpipe-fd.c for details.
Plugin Entry Points
This section will describe each of the entry points (subroutines) within the plugin that the plugin must provide for Bacula, when they are called and their arguments. As noted above, pointers to these subroutines are passed back to Bacula in the pFuncs structure when Bacula calls the loadPlugin() externally defined entry point.
newPlugin(bpContext *ctx)
This is the entry point that Bacula will call when a new "instance" of the plugin is created. This typically happens at the beginning of a Job. If 10 Jobs are running simultaneously, there will be at least 10 instances of the plugin.The bpContext structure will be passed to the plugin, and during this call, if the plugin needs to have its private working storage that is associated with the particular instance of the plugin, it should create it from the heap (malloc the memory) and store a pointer to its private working storage in the pContext variable. Note: since Bacula is a multi-threaded program, you must not keep any variable data in your plugin unless it is truly meant to apply globally to the whole plugin. In addition, you must be aware that except the first and last call to the plugin (loadPlugin and unloadPlugin) all the other calls will be made by threads that correspond to a Bacula job. The bpContext that will be passed for each thread will remain the same throughout the Job thus you can keep your private Job specific data in it (bContext).
typedef struct s_bpContext {
void *pContext; /* Plugin private context */
void *bContext; /* Bacula private context */
} bpContext;
This context pointer will be passed as the first argument to all the entry points that Bacula calls within the plugin. Needless to say, the plugin should not change the bContext variable, which is Bacula's private context pointer for this instance (Job) of this plugin.
freePlugin(bpContext *ctx)
This entry point is called when the this instance of the plugin is no longer needed (the Job is ending), and the plugin should release all memory it may have allocated for this particular instance (Job) i.e. the pContext. This is not the final termination of the plugin signaled by a call to unloadPlugin. Any other instances (Job) will continue to run, and the entry point newPlugin may be called again if other jobs start.
getPluginValue(bpContext *ctx, pVariable var, void *value)
Bacula will call this entry point to get a value from the plugin. This entry point is currently not called.
setPluginValue(bpContext *ctx, pVariable var, void *value)
Bacula will call this entry point to set a value in the plugin. This entry point is currently not called.
handlePluginEvent(bpContext *ctx, bEvent *event, void *value)
This entry point is called when Bacula encounters certain events (discussed below). This is, in fact, the main way that most plugins get control when a Job runs and how they know what is happening in the job. It can be likened to the RunScript feature that calls external programs and scripts. When the plugin is called, Bacula passes it the pointer to an event structure (bEvent), which currently has one item, the eventType:
typedef struct s_bEvent {
uint32_t eventType;
} bEvent;
which defines what event has been triggered, and for each event, Bacula will pass a pointer to a value associated with that event. If no value is associated with a particular event, Bacula will pass a NULL pointer, so the plugin must be careful to always check value pointer prior to dereferencing it.
The current list of events are:
typedef enum {
bEventJobStart = 1,
bEventJobEnd = 2,
bEventStartBackupJob = 3,
bEventEndBackupJob = 4,
bEventStartRestoreJob = 5,
bEventEndRestoreJob = 6,
bEventStartVerifyJob = 7,
bEventEndVerifyJob = 8,
bEventBackupCommand = 9,
bEventRestoreCommand = 10,
bEventLevel = 11,
bEventSince = 12,
bEventCancelCommand = 13, /* Executed by another thread */
/* Just before bEventVssPrepareSnapshot */
bEventVssBackupAddComponents = 14,
bEventVssRestoreLoadComponentMetadata = 15,
bEventVssRestoreSetComponentsSelected = 16,
bEventRestoreObject = 17,
bEventEndFileSet = 18,
bEventPluginCommand = 19,
bEventVssBeforeCloseRestore = 21,
/* Add drives to VSS snapshot
* argument: char[27] drivelist
* You need to add them without duplicates,
* see fd_common.h add_drive() copy_drives() to get help
*/
bEventVssPrepareSnapshot = 22,
bEventOptionPlugin = 23,
bEventHandleBackupFile = 24 /* Used with Options Plugin */
} bEventType;
Most of the above are self-explanatory.
- bEventJobStart
- is called whenever a Job starts. The value passed is a pointer to a string that contains: "Jobid=nnn Job=job-name". Where nnn will be replaced by the JobId and job-name will be replaced by the Job name. The variable is temporary so if you need the values, you must copy them.
- bEventJobEnd
- is called whenever a Job ends. No value is passed.
- bEventStartBackupJob
- is called when a Backup Job begins. No value is passed.
- bEventEndBackupJob
- is called when a Backup Job ends. No value is passed.
- bEventStartRestoreJob
- is called when a Restore Job starts. No value is passed.
- bEventEndRestoreJob
- is called when a Restore Job ends. No value is passed.
- bEventStartVerifyJob
- is called when a Verify Job starts. No value is passed.
- bEventEndVerifyJob
- is called when a Verify Job ends. No value is passed.
- bEventBackupCommand
- is called prior to the bEventStartBackupJob and the plugin is passed the command string (everything after the equal sign in "Plugin =" as the value.
Note, if you intend to backup a file, this is an important first point to write code that copies the command string passed into your pContext area so that you will know that a backup is being performed and you will know the full contents of the "Plugin =" command (i.e. what to backup and what virtual filename the user wants to call it.
- bEventRestoreCommand
- is called prior to the bEventStartRestoreJob and the plugin is passed the command string (everything after the equal sign in "Plugin =" as the value.
See the notes above concerning backup and the command string. This is the point at which Bacula passes you the original command string that was specified during the backup, so you will want to save it in your pContext area for later use when Bacula calls the plugin again.
- bEventLevel
- is called when the level is set for a new Job. The value is a 32 bit integer stored in the void*, which represents the Job Level code.
- bEventSince
- is called when the since time is set for a new Job. The value is a time_t time at which the last job was run.
- bEventCancelCommand
- is called whenever the currently running Job is cancelled. Be warned that this event is sent by a different thread.
- bEventVssBackupAddComponents
-
- bEventPluginCommand
- is called for each PluginCommand present in the current FileSet. The event will be sent only on plugin specifed in the command. The argument is the PluginCommand (not valid after the call).
- bEventHandleBackupFile
- is called for each file of a FileSet when using a Options Plugin. If the plugin returns CF_OK, it will be used for the backup, if it returns CF_SKIP, the file will be skipped. Anything else will backup the file with Bacula core functions.
During each of the above calls, the plugin receives either no specific value or only one value, which in some cases may not be sufficient. However, knowing the context of the event, the plugin can call back to the Bacula entry points it was passed during the loadPlugin call and get to a number of Bacula variables. (at the current time few Bacula variables are implemented, but it easily extended at a future time and as needs require).
startBackupFile(bpContext *ctx, struct save_pkt *sp)
This entry point is called only if your plugin is a command plugin, and it is called when Bacula encounters the "Plugin = " directive in the Include section of the FileSet. Called when beginning the backup of a file. Here Bacula provides you with a pointer to the save_pkt structure and you must fill in this packet with the "attribute" data of the file.
struct save_pkt {
int32_t pkt_size; /* size of this packet */
char *fname; /* Full path and filename */
char *link; /* Link name if any */
struct stat statp; /* System stat() packet for file */
int32_t type; /* FT_xx for this file */
uint32_t flags; /* Bacula internal flags */
bool portable; /* set if data format is portable */
char *cmd; /* command */
uint32_t delta_seq; /* Delta sequence number */
char *object_name; /* Object name to create */
char *object; /* restore object data to save */
int32_t object_len; /* restore object length */
int32_t index; /* restore object index */
int32_t pkt_end; /* end packet sentinel */
};
The second argument is a pointer to the save_pkt structure for the file to be backed up. The plugin is responsible for filling in all the fields of the save_pkt. If you are backing up a real file, then generally, the statp structure can be filled in by doing a stat system call on the file.
If you are backing up a database or something that is more complex, you might want to create a virtual file. That is a file that does not actually exist on the filesystem, but represents say an object that you are backing up. In that case, you need to ensure that the fname string that you pass back is unique so that it does not conflict with a real file on the system, and you need to artifically create values in the statp packet.
Example programs such as bpipe-fd.c show how to set these fields. You must take care not to store pointers the stack in the pointer fields such as fname and link, because when you return from your function, your stack entries will be destroyed. The solution in that case is to malloc() and return the pointer to it. In order to not have memory leaks, you should store a pointer to all memory allocated in your pContext structure so that in subsequent calls or at termination, you can release it back to the system.
Once the backup has begun, Bacula will call your plugin at the pluginIO entry point to "read" the data to be backed up. Please see the bpipe-fd.c plugin for how to do I/O.
Example of filling in the save_pkt as used in bpipe-fd.c:
struct plugin_ctx *p_ctx = (struct plugin_ctx *)ctx->pContext; time_t now = time(NULL); sp->fname = p_ctx->fname; sp->statp.st_mode = 0700 | S_IFREG; sp->statp.st_ctime = now; sp->statp.st_mtime = now; sp->statp.st_atime = now; sp->statp.st_size = -1; sp->statp.st_blksize = 4096; sp->statp.st_blocks = 1; p_ctx->backup = true; return bRC_OK;
Note: the filename to be created has already been created from the command string previously sent to the plugin and is in the plugin context (p_ctx→fname) and is a malloc()ed string. This example creates a regular file (S_IFREG), with various fields being created.
In general, the sequence of commands issued from Bacula to the plugin to do a backup while processing the "Plugin = " directive are:
- generate a bEventBackupCommand event to the specified plugin and pass it the command string.
- make a startPluginBackup call to the plugin, which fills in the data needed in save_pkt to save as the file attributes and to put on the Volume and in the catalog.
- call Bacula's internal save_file() subroutine to save the specified file. The plugin will then be called at pluginIO() to "open" the file, and then to read the file data. Note, if you are dealing with a virtual file, the "open" operation is something the plugin does internally and it doesn't necessarily mean opening a file on the filesystem. For example in the case of the bpipe-fd.c program, it initiates a pipe to the requested program. Finally when the plugin signals to Bacula that all the data was read, Bacula will call the plugin with the "close" pluginIO() function.
endBackupFile(bpContext *ctx)
Called at the end of backing up a file for a command plugin. If the plugin's work is done, it should return bRC_OK. If the plugin wishes to create another file and back it up, then it must return bRC_More (not yet implemented). This is probably a good time to release any malloc()ed memory you used to pass back filenames.
startRestoreFile(bpContext *ctx, const char *cmd)
Called when the first record is read from the Volume that was previously written by the command plugin.
createFile(bpContext *ctx, struct restore_pkt *rp)
Called for a command plugin to create a file during a Restore job before restoring the data. This entry point is called before any I/O is done on the file. After this call, Bacula will call pluginIO() to open the file for write.The data in the restore_pkt is passed to the plugin and is based on the data that was originally given by the plugin during the backup and the current user restore settings (e.g. where, RegexWhere, replace). This allows the plugin to first create a file (if necessary) so that the data can be transmitted to it. The next call to the plugin will be a pluginIO command with a request to open the file write-only.
This call must return one of the following values:
enum {
CF_SKIP = 1, /* skip file (not newer or something) */
CF_ERROR, /* error creating file */
CF_EXTRACT, /* file created, data to extract */
CF_CREATED, /* file created, no data to extract */
CF_CORE /* let bacula core handles the file creation */
};
in the restore_pkt value create_status. For a normal file, unless there is an error, you must return CF_EXTRACT.
struct restore_pkt {
int32_t pkt_size; /* size of this packet */
int32_t stream; /* attribute stream id */
int32_t data_stream; /* id of data stream to follow */
int32_t type; /* file type FT */
int32_t file_index; /* file index */
int32_t LinkFI; /* file index to data if hard link */
uid_t uid; /* userid */
struct stat statp; /* decoded stat packet */
const char *attrEx; /* extended attributes if any */
const char *ofname; /* output filename */
const char *olname; /* output link name */
const char *where; /* where */
const char *RegexWhere; /* regex where */
int replace; /* replace flag */
int create_status; /* status from createFile() */
int32_t pkt_end; /* end packet sentinel */
};
Typical code to create a regular file would be the following:
struct plugin_ctx *p_ctx = (struct plugin_ctx *)ctx->pContext; time_t now = time(NULL); sp->fname = p_ctx->fname; /* set the full path/filename I want to create */ sp->type = FT_REG; sp->statp.st_mode = 0700 | S_IFREG; sp->statp.st_ctime = now; sp->statp.st_mtime = now; sp->statp.st_atime = now; sp->statp.st_size = -1; sp->statp.st_blksize = 4096; sp->statp.st_blocks = 1; return bRC_OK;
This will create a virtual file. If you are creating a file that actually exists, you will most likely want to fill the statp packet using the stat() system call.
Creating a directory is similar, but requires a few extra steps:
struct plugin_ctx *p_ctx = (struct plugin_ctx *)ctx->pContext; time_t now = time(NULL); sp->fname = p_ctx->fname; /* set the full path I want to create */ sp->link = xxx; where xxx is p_ctx->fname with a trailing forward slash sp->type = FT_DIREND sp->statp.st_mode = 0700 | S_IFDIR; sp->statp.st_ctime = now; sp->statp.st_mtime = now; sp->statp.st_atime = now; sp->statp.st_size = -1; sp->statp.st_blksize = 4096; sp->statp.st_blocks = 1; return bRC_OK;
The link field must be set with the full cononical path name, which always ends with a forward slash. If you do not terminate it with a forward slash, you will surely have problems later.
As with the example that creates a file, if you are backing up a real directory, you will want to do an stat() on the directory.
Note, if you want the directory permissions and times to be correctly restored, you must create the directory after all the file directories have been sent to Bacula. That allows the restore process to restore all the files in a directory using default directory options, then at the end, restore the directory permissions. If you do it the other way around, each time you restore a file, the OS will modify the time values for the directory entry.
setFileAttributes(bpContext *ctx, struct restore_pkt *rp)
This is call not yet implemented. Called for a command plugin.See the definition of restre_pkt in the above section.
endRestoreFile(bpContext *ctx)
Called when a command plugin is done restoring a file.
pluginIO(bpContext *ctx, struct io_pkt *io)
Called to do the input (backup) or output (restore) of data from or to a file for a command plugin. These routines simulate the Unix read(), write(), open(), close(), and lseek() I/O calls, and the arguments are passed in the packet and the return values are also placed in the packet. In addition for Win32 systems the plugin must return two additional values (described below).
enum {
IO_OPEN = 1,
IO_READ = 2,
IO_WRITE = 3,
IO_CLOSE = 4,
IO_SEEK = 5
};
struct io_pkt {
int32_t pkt_size; /* Size of this packet */
int32_t func; /* Function code */
int32_t count; /* read/write count */
mode_t mode; /* permissions for created files */
int32_t flags; /* Open flags */
char *buf; /* read/write buffer */
const char *fname; /* open filename */
int32_t status; /* return status */
int32_t io_errno; /* errno code */
int32_t lerror; /* Win32 error code */
int32_t whence; /* lseek argument */
boffset_t offset; /* lseek argument */
bool win32; /* Win32 GetLastError returned */
int32_t pkt_end; /* end packet sentinel */
};
The particular Unix function being simulated is indicated by the func, which will have one of the IO_OPEN, IO_READ, ... codes listed above. The status code that would be returned from a Unix call is returned in status for IO_OPEN, IO_CLOSE, IO_READ, and IO_WRITE. The return value for IO_SEEK is returned in offset which in general is a 64 bit value.
When there is an error on Unix systems, you must always set io_error, and on a Win32 system, you must always set win32, and the returned value from the OS call GetLastError() in lerror.
For all except IO_SEEK, status is the return result. In general it is a positive integer unless there is an error in which case it is -1.
The following describes each call and what you get and what you should return:
- IO_OPEN
- You will be passed fname, mode, and flags. You must set on return: status, and if there is a Unix error io_errno must be set to the errno value, and if there is a Win32 error win32 and lerror.
- IO_READ
- You will be passed: count, and buf (buffer of size count). You must set on return: status to the number of bytes read into the buffer (buf) or -1 on an error, and if there is a Unix error io_errno must be set to the errno value, and if there is a Win32 error, win32 and lerror must be set.
- IO_WRITE
- You will be passed: count, and buf (buffer of size count). You must set on return: status to the number of bytes written from the buffer (buf) or -1 on an error, and if there is a Unix error io_errno must be set to the errno value, and if there is a Win32 error, win32 and lerror must be set.
- IO_CLOSE
- Nothing will be passed to you. On return you must set status to 0 on success and -1 on failure. If there is a Unix error io_errno must be set to the errno value, and if there is a Win32 error, win32 and lerror must be set.
- IO_LSEEK
- You will be passed: offset, and whence. offset is a 64 bit value and is the position to seek to relative to whence. whence is one of the following SEEK_SET, SEEK_CUR, or SEEK_END indicating to either to seek to an absolute possition, relative to the current position or relative to the end of the file. You must pass back in offset the absolute location to which you seeked. If there is an error, offset should be set to -1. If there is a Unix error io_errno must be set to the errno value, and if there is a Win32 error, win32 and lerror must be set.
Note: Bacula will call IO_SEEK only when writing a sparse file.
bool checkFile(bpContext *ctx, char *fname)
If this entry point is set, Bacula will call it after backing up all file data during an Accurate backup. It will be passed the full filename for each file that Bacula is proposing to mark as deleted. Only files previously backed up but not backed up in the current session will be marked to be deleted. If you return false, the file will be be marked deleted. If you return true the file will not be marked deleted. This permits a plugin to ensure that previously saved virtual files or files controlled by your plugin that have not change (not backed up in the current job) are not marked to be deleted. This entry point will only be called during Accurate Incrmental and Differential backup jobs.
Bacula Plugin Entrypoints
When Bacula calls one of your plugin entrypoints, you can call back to the entrypoints in Bacula that were supplied during the xxx plugin call to get or set information within Bacula.
bRC registerBaculaEvents(bpContext *ctx, ...)
This Bacula entrypoint will allow you to register to receive events that are not autmatically passed to your plugin by default. This entrypoint currently is unimplemented.
bRC getBaculaValue(bpContext *ctx, bVariable var, void *value)
Calling this entrypoint, you can obtain specific values that are available in Bacula. The following Variables can be referenced:- bVarJobId returns an int
- bVarFDName returns a char *
- bVarLevel returns an int
- bVarClient returns a char *
- bVarJobName returns a char *
- bVarJobStatus returns an int
- bVarSinceTime returns an int (time_t)
- bVarAccurate returns an int
bRC setBaculaValue(bpContext *ctx, bVariable var, void *value)
Calling this entrypoint allows you to set particular values in Bacula. The only variable that can currently be set is bVarFileSeen and the value passed is a char * that points to the full filename for a file that you are indicating has been seen and hence is not deleted.
bRC JobMessage(bpContext *ctx, const char *file, int line, int type, utime_t mtime, const char *fmt, ...)
This call permits you to put a message in the Job Report.
bRC DebugMessage(bpContext *ctx, const char *file, int line, int level, const char *fmt, ...)
This call permits you to print a debug message.
void baculaMalloc(bpContext *ctx, const char *file, int line, size_t size)
This call permits you to obtain memory from Bacula's memory allocator.
void baculaFree(bpContext *ctx, const char *file, int line, void *mem)
This call permits you to free memory obtained from Bacula's memory allocator.
Building Bacula Plugins
There is currently one sample program example-plugin-fd.c and one working plugin bpipe-fd.c that can be found in the Bacula src/plugins/fd directory. Both are built with the following:cd <bacula-source> ./configure <your-options> make ... cd src/plugins/fd make make test
After building Bacula and changing into the src/plugins/fd directory, the make command will build the bpipe-fd.so plugin, which is a very useful and working program.
The make test command will build the example-plugin-fd.so plugin and a binary named main, which is build from the source code located in src/filed/fd_plugins.c.
If you execute ./main, it will load and run the example-plugin-fd plugin simulating a small number of the calling sequences that Bacula uses in calling a real plugin. This allows you to do initial testing of your plugin prior to trying it with Bacula.
You can get a good idea of how to write your own plugin by first studying the example-plugin-fd, and actually running it. Then it can also be instructive to read the bpipe-fd.c code as it is a real plugin, which is still rather simple and small.
When actually writing your own plugin, you may use the example-plugin-fd.c code as a template for your code.
Advanced Restore Options
Some plugins can be configured at the restore time with “Plugin Restore Objects” stored in the catalog. It is possible to list these objects and display them for a list job jobids with the following command:
# /opt/bacula/bin/bconsole
*.bvfs_get_jobids client=127.0.0.1-fd
10,11,12
*llist pluginrestoreconf jobid=10,11,12
jobid: 10
restoreobjectid: 15
objectname: RestoreOptions
pluginname: bpipe:/@bpipe@/encrypt-bug.jpg:cat /tmp/encrypt-bug.jpg:cat >/tmp/encrypt-bug.jpg
objecttype: 27
*list pluginrestoreconf jobid=10,11,12 id=15
# Plugin configuration file
# Version 1
OptPrompt="Restore command to use"
restore_command=@STR@
In this example, the bpipe plugin can be configured at restore time to overwrite the default restore command with a string (@STR@).
From a script it is possible to use the “Plugin Restore Option” menu at the restore step, or to submit a file with the appropriate configuration. For the bpipe plugin, the “restore_command” can be configured at the restore time. With the bpipe plugin, the “Plugin Restore Option” file would look like:
# cat /tmp/restore.opts restore_command="cat > /tmp/a.jpg"
The file should be uploaded to the director during the restore session and used in the restore command via the pluginrestoreconf option. The file transfer and the restore command should be done in the same bconsole session.
# /opt/bacula/bin/bconsole *@putfile akey /tmp/restore.opts OK *restore pluginrestoreconf="15:akey"
The “pluginrestoreconf” option of the restore command needs two parameters:
- RestoreObjectId displayed in the “llist pluginrestoreconf” command
- The Key of the file uploaded to the Director with the @putfile command
The “RestoreObjectId” is used to check the validity of the options provided by the user.
Bacula Auth Plugin Documentation
Overview
Large companies are using central systems to handle authentication and authorization data. It is very often based on LDAP databases. With one click, the access to all software in the company can be granted or revoked. Today, once a user can access the bconsole.conf file, Bacula doesn't require any other form of authentication, basically, any user that have access to bconsole.conf can interact with Bacula. It is mandatory to change the Console resource and reload the Director to disable a user. The idea would be to let the administrator the possibility to authenticate users with a central database. For that, this document propose to design an Authorization/Authentication mechanism based on a Director plugin. Once the Console is properly connected, the plugin would be able to authenticate a given user (password/user), and in a second time, would be also able to manage ACLs.
Dictionary
- Authentication
- is the act of proving an assertion, such as the identity of a computer system user. In contrast with identification, the act of indicating a person or thing's identity, authentication is the process of verifying that identity. It might involve validating with personal password.
- Authorization
- is the function of specifying access rights/privileges to resources, which is related to information security and computer security in general and to access control in particular. More formally, "to authorize" is to define an access policy.
- Multi-factor authentication
- (or MFA) is an authentication method in which a computer user is granted access only after successfully presenting two or more pieces of evidence (or factors) to an authentication mechanism: knowledge (something the user and only the user knows), possession (something the user and only the user has), and inherence (something the user and only the user is).
- Two-Factor Authentication
- (or 2FA) is a subset of MFA described above with only two different factors, i.e. something they know, something they have, or something they are.
Bacula DIR Plugin API
To write a Bacula plugin, you create a dynamic shared object program (or dll on Win32) with a particular name and two exported entry points, place it in the Plugins Directory, which is defined in the bacula-dir.conf file in the Director resource, and when the Director starts, it will load all the plugins that end with -dir.so (or -dir.dll on Win32) found in that directory.
Loading Plugins
Once the Director loads the plugins, it asks the dynamic loader for the two entry points (loadPlugin and unloadPlugin) then calls the loadPlugin entry point (see below). Bacula passes information to the plugin through this call and it gets back information that it needs to use the plugin. Later, Bacula will call particular functions that are defined by the loadPlugin interface. When Bacula is finished with the plugin (when Bacula is going to exit), it will call the unloadPlugin entry point.
The two entry points are:
bRC loadPlugin(bDirInfo *lbinfo, bDirFuncs *lbfuncs, pDirInfo **pinfo, pDirFuncs **pfuncs)
and
bRC unloadPlugin()
both these external entry points to the shared object are defined as C entry points to avoid name mangling complications with C++. However, the shared object can actually be written in any language (preferably C or C++) providing that it follows C language calling conventions.
The definitions for bRC and the arguments are src/dird/dir_plugins.h and so this header file needs to be included in your plugin. It along with src/lib/plugins.h define basically the whole plugin interface. Within this header file, it includes the following files:
#include <sys/types.h> #include "config.h" #include "bc_types.h" #include "lib/plugins.h"
loadPlugin
As previously mentioned, the loadPlugin entry point in the plugin is called immediately after Bacula loads the plugin when the Director itself is first starting. This entry point is only called once during the execution of the Director. In calling the plugin, the first two arguments are information from Bacula that is passed to the plugin, and the last two arguments are information about the plugin that the plugin must return to Bacula. The call is:
bRC loadPlugin(bDirInfo *lbinfo, bDirFuncs *lbfuncs, pDirInfo **pinfo, pDirFuncs **pfuncs)
and the arguments are:
- lbinfo
- This is information about Bacula in general. Currently, the only value defined in the bInfo structure is the version, which is the Bacula plugin interface version, currently defined as 1. The size is set to the byte size of the structure. The exact definition of the bInfo structure as of this writing is:
typedef struct s_dirbaculaInfo { uint32_t size; uint32_t version; } bDirInfo; - lbfuncs
- The bFuncs structure defines the callback entry points within Bacula that the plugin can use register events, get Bacula values, set Bacula values, and send messages to the Job output or debug output. The exact definition as of this writing is:
typedef struct s_dirbaculaFuncs { uint32_t size; uint32_t version; bRC (*registerBaculaEvents)(bpContext *ctx, ...); bRC (*getBaculaValue)(bpContext *ctx, brDirVariable var, void *value); bRC (*setBaculaValue)(bpContext *ctx, bwDirVariable var, void *value); bRC (*JobMessage)(bpContext *ctx, const char *file, int line, int type, utime_t mtime, const char *fmt, ...); bRC (*DebugMessage)(bpContext *ctx, const char *file, int line, int level, const char *fmt, ...); } bDirFuncs;We will discuss these entry points and how to use them a bit later when describing the plugin code.
- pInfo
- When the loadPlugin entry point is called, the plugin must initialize an information structure about the plugin and return a pointer to this structure to Bacula. The exact definition as of this writing is:
typedef struct s_dirpluginInfo { uint32_t size; uint32_t version; const char *plugin_magic; const char *plugin_license; const char *plugin_author; const char *plugin_date; const char *plugin_version; const char *plugin_description; } pDirInfo;Where:
- version
- is the current Bacula defined plugin interface version, currently set to 1. If the interface version differs from the current version of Bacula, the plugin will not be run (not yet implemented).
- plugin_magic
- is a pointer to the text string DirPluginData defined in DIR_PLUGIN_MAGIC, a sort of sanity check. If this value is not specified, the plugin will not be run (not yet implemented).
- plugin_license
- is a pointer to a text string that describes the plugin license. Bacula will only accept compatible licenses. The accepted licenses as of this writing are: "Bacula AGPLv3", "AGPLv3", "Bacula Systems(R) SA" and defined in BPLUGIN_LICENSE compile time definition.
- plugin_author
- is a pointer to the text name of the author of the plugin. This string can be anything but is generally the authorâs name.
- plugin_date
- is the pointer to a text string containing the date of the plugin. This string can be anything but is generally some human readable form of the date.
- plugin_version
- is a pointer to a text string containing the version of the plugin. The contents are determined by the plugin writer.
- plugin_description
- is a pointer to a text string describing what the plugin does. The contents are determined by the plugin writer.
The pInfo structure must be defined in static memory because Bacula does not copy it and may refer to the values at any time while the plugin is loaded. All values must be supplied or the plugin will not run (not yet implemented). All text strings must be either ASCII or UTF-8 strings that are terminated with a zero (nul) byte.
- pFuncs
- When the loadPlugin entry point is called, the plugin must initialize an entry point structure about the plugin and return a pointer to this structure to Bacula. This structure contains pointer to each of the entry points that the plugin must (or will) provide for Bacula. When Bacula is actually running the plugin, it will call the defined entry points at particular times. The pFuncs structure must be defined in static memory because Bacula does not copy it and may refer to the values at any time while the plugin is loaded.
The exact definition as of this writing is:
typedef struct s_dirpluginFuncs { uint32_t size; uint32_t version; bRC (*newPlugin)(bpContext *ctx); bRC (*freePlugin)(bpContext *ctx); bRC (*getPluginValue)(bpContext *ctx, pDirVariable var, void *value); bRC (*setPluginValue)(bpContext *ctx, pDirVariable var, void *value); bRC (*handlePluginEvent)(bpContext *ctx, bDirEvent *event, void *value); bRC (*getPluginAuthenticationData)(bpContext *ctx, const char *param, void **data); bRC (*getPluginAuthorizationData)(bpContext *ctx, const char *param, void **data); } pDirFuncs;The details of the entry points will be presented in separate sections below. Where:
- size
- is the byte size of the structure.
- version
- is the plugin interface version currently set to 1 (defined in DIR_PLUGIN_INTERFACE_VERSION).
*
unloadPluginAs previously mentioned, the unloadPlugin entry point in the plugin is called just before a Director finish execution. This entry point is responsible for releasing any resources allocated by plugin during loadPlugin.
Plugin Entry Points
This section will describe each of the entry points (subroutines) within the plugin that the plugin must provide for Bacula, when they are called and their arguments. As noted above, pointers to these subroutines are passed back to Bacula in the pFuncs structure when Bacula calls the loadPlugin() externally defined entry point.
newPlugin
This is the entry point that Bacula will call when a new instance of the plugin is created. This typically happens at the beginning of any Job or Console connection. If 10 Jobs are running simultaneously, there will be at least 10 instances of the plugin.
The bpContext structure will be passed to the plugin, and during this call, if the plugin needs to have its private working storage that is associated with the particular instance of the plugin, it should create it from the heap (malloc the memory) and store a pointer to its private working storage in the pContext variable.
Note: since Bacula is a multi-threaded program, you must not keep any variable data in your plugin unless it is truly meant to apply globally to the whole plugin. In addition, you must be aware that except the first and last call to the plugin (loadPlugin and unloadPlugin) all the other calls will be made by threads that correspond to a Bacula job. The bpContext that will be passed for each thread will remain the same throughout the Job thus you can keep your private Job specific data in it (bContext).
typedef struct s_bpContext {
void *pContext; /* Plugin private context */
void *bContext; /* Bacula private context */
} bpContext;
This context pointer will be passed as the first argument to all the entry points that Bacula calls within the plugin. Needless to say, the plugin should not change the bContext variable, which is Baculaâs private context pointer for this instance (Job) of this plugin.
freePlugin
This entry point is called when the this instance of the plugin is no longer needed (the Job/Console is ending), and the plugin should release all memory it may have allocated for this particular instance i.e. the pContext. This is not the final termination of the plugin signaled by a call to unloadPlugin. Any other instances (Job) will continue to run, and the entry point newPlugin may be called again if other jobs start.
getPluginValue
Bacula will call this entry point to get a value from the plugin. This entry point is currently not called.
setPluginValue
Bacula will call this entry point to set a value in the plugin. This entry point is currently not called.
handlePluginEvent
This entry point is called when Bacula encounters certain events. This is, in fact, the main way that most plugins get control when a Job/Console runs and how they know what is happening in the job. It can be likened to the RunScript feature that calls external programs and scripts. When the plugin is called, Bacula passes it the pointer to an event structure (bDirEvent), which currently has one item, the eventType:
typedef struct s_bDirEvent {
uint32_t eventType;
} bDirEvent;
which defines what event has been triggered, and for each event, Bacula will pass a pointer to a value associated with that event. If no value is associated with a particular event, Bacula will pass a NULL pointer, so the plugin must be careful to always check value pointer prior to dereferencing it.
The current list of events are:
typedef enum {
bDirEventJobStart = 1,
bDirEventJobEnd = 2,
bDirEventJobInit = 3,
bDirEventJobRun = 4,
bDirEventVolumePurged = 5,
bDirEventNewVolume = 6,
bDirEventNeedVolume = 7,
bDirEventVolumeFull = 8,
bDirEventRecyle = 9,
bDirEventGetScratch = 10,
bDirEventAuthenticationQuestion = 1000, // *value is a bDirAuthValue struct allocated by Dir
// to get return value from
bDirEventAuthenticationResponse = 1001, // *value is a char* to user response
bDirEventAuthenticate = 1002, // return bRC_OK when authenticate is successful
} bDirEventsType;
Most of the above are self-explanatory.
- bEventJobStart
- is called whenever a Job starts.
- bEventJobEnd
- is called whenever a Job ends. No value is passed.
- bDirEventJobInit
- is called when ... .
- bDirEventJobRun
- is called when ... .
- bDirEventVolumePurged
- is called when ... .
- bDirEventAuthenticationQuestion
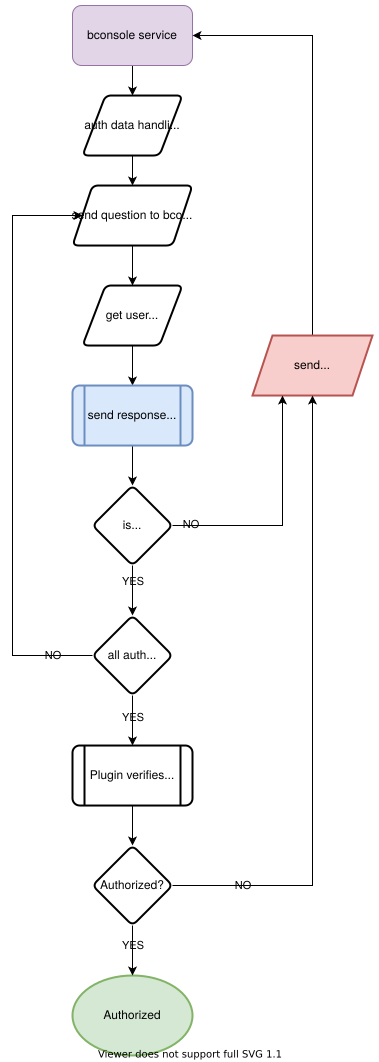
- is called for authentication plugin (see description below - BPAM) whenever Director wants to get the next question in user (bconsole) authentication session. A value is a pointer to bDirAuthValue. Plugin should return a single bDirAuthData structure (described below) in this value.
- bDirEventAuthenticationResponse
- is called for authentication plugin to forward user response for the last handled authentication question. A value is a pointer to bDirAuthValue. Plugin will get a response in value->response (as a char*, a nul terminated string) and value->seqdata copied from authentication question. Plugin should return bRC_OK if Director can proceed to the next step.
- bDirEventAuthenticate
- is called for authentication plugin whenever Director asks a plugin to final authenticate result where bRC_OK when successful and bRC_Error when error.
During each of the above calls, the plugin receives either no specific value or only one value, which in some cases may not be sufficient. However, knowing the context of the event, the plugin can call back to the Bacula entry points it was passed during the loadPlugin call and get to a number of Bacula variables. (at the current time few Bacula variables are implemented, but it easily extended at a future time and as needs require).
Bacula Pluggable Authentication Modules API Framework BPAM]
Starting from Bacula Enterprise 12.6 new user authentication API framework is introduced which allows to configure a different authentication mechanisms (user credentials verification) using a dedicated Director plugins and Console resource configuration. This is called BPAM - Bacula Pluggable Authentication Modules.
The new framework support standard user/password and MFA authentication schemes which are fully driven by external plugins. On the client side bconsole when noticed will perform user interaction to collect required credentials. Bacula will still support all previous authentication schemas including CRAM-MD5 and TLS. You can even configure TLS Authentication together with new BPAM authentication raising required security level. BPAM authentication is available for named Console resources only.
The BPAM framework extend a standard Director Plugin API architecture with the following plugin entry points:
bRC getPluginAuthenticationData(bpContext *ctx, const char *param, void **data); bRC getPluginAuthorizationData(bpContext *ctx, const char *param, void **data);
and plugin events mentioned above:
...
bDirEventAuthenticationQuestion = 1000, // *value is a bDirAuthValue struct allocated by Dir
// to get return value from
bDirEventAuthenticationResponse = 1001, // *value is a char* to user response
bDirEventAuthenticate = 1002, // return bRC_OK when authenticate is successful
...
BPAM Plugin registration
BPAM assumes that any authentication or authorization workflows manages a very sensitive information (user credentials or permissions) which must be handled with extreme care, i.e. it should not be visible outside the selected plugin. This makes a clear break in general Bacula's plugin workflow design where every event is forwarded to every plugin until one of them raise event handling is done. This kind of event workflow handling can leads to unexpected user credentials data breach which is unacceptable.
Before a plugin will get authentication or authorization requests it has to register its services with getPluginAuthenticationData() or getPluginAuthorizationData() plugin entry points. Director will call this plugin's functions (if defined in pDirFuncs structure) on every new bconsole connection for selected plugin only when appropriate Console resource is configured (see below for more info).
Console {
Name = "bpamauthconsole"
Password = "xxx"
# New directives
Authentication Plugin = "<plugin>:<optional parameters>"
Authorization Plugin = "<plugin>:<optional parameters>" # not implemented yet!
...
}
bacula-dir.conf - Console resource configuration
The entry point getPluginAuthenticationData() is called when Director needs to forward authentication to selected <plugin> which is defined with Authentication Plugin = ... parameter. The name <plugin> has to match the filename of the Director plugin (without a -dir.* suffix). No other plugin will be bothered. The function takes the following parameters:
- param
- is a nul terminated string defined on the right side of the parameter, including plugin name and optional plugin parameters.
- data
- is a pointer to bDirAuthenticationRegister struct pointer (bDirAuthenticationRegister**) which should be filled as a return value for plugin data registration.
The bDirAuthenticationRegister structure is defined as:
typedef struct s_bDirAuthenticationRegister {
const char * name;
const char * welcome;
const uint32_t num;
const bDirAuthenticationData *data;
const int32_t nsTTL;
} bDirAuthenticationRegister;
which together with bDirAuthenticationData structure will define a full authentication workflow managed by this plugin. Where parameters are:
- name
- is a name of the authentication plugin and should match the <plugin> string in Console resource configuration.
- welcome
- is an optional authentication welcome string which will be displayed before first authentication question.
- num
- is a number of elements in authentication operation data table pointed by data below.
- data
- the pointer to the authentication operation data (bDirAuthenticationData) table, the first element, with a number of elements defined in num above.
- nsTTL
- currently unimplemented, for future usage.
The structure bDirAuthenticationData is defines as:
typedef struct s_bDirAuthenticationData {
const bDirAuthenticationOperation operation;
const char * question;
const uint32_t seqdata;
} bDirAuthenticationData;
where:
- operation
- a single authentication step (operation) which should be performed by Director + bconsole application. The list of possible operations include: display user the message, get login from user, get password from user, etc.
- question
- the nul terminated string to display to the user during credentials collection.
- seqdata
- 32 bit integer for full plugin use; this value will be added to the user response send to the plugin.
Both bDirAuthenticationRegister and bDirAuthenticationData structures could be a statically compiled data or assembled in runtime. Director will read data from it and never change. BPAM defines the following authentication operations:
typedef enum {
bDirAuthenticationOperationPlugin,
bDirAuthenticationOperationPluginAll,
bDirAuthenticationOperationMessage,
bDirAuthenticationOperationPlain,
bDirAuthenticationOperationLogin = bDirAuthenticationOperationPlain,
bDirAuthenticationOperationHidden,
bDirAuthenticationOperationPassword = bDirAuthenticationOperationHidden,
bDirAuthenticationOperationAuthenticate,
} bDirAuthenticationOperation;
- bDirAuthenticationOperationPlugin
- Director will get the current operation from the plugin using bDirEventAuthenticationQuestion plugin event, then it should execute the operation returned.
- bDirAuthenticationOperationPluginAll
- Director will get all authentication operations from the plugin with bDirEventAuthenticationQuestion plugin events loop.
- bDirAuthenticationOperationMessage
- Director will ask bconsole to display a message pointed by bDirAuthenticationData.question and will proceed to the next operation in the list.
- bDirAuthenticationOperationPlain
- (alias bDirAuthenticationOperationLogin) Director will ask bconsole to display a message pointed by bDirAuthenticationData.question, then get plain input visible to the user and proceed to the next operation in the list.
- bDirAuthenticationOperationHidden
- (alias bDirAuthenticationOperationPassword) Director will ask bconsole to display a message pointed by bDirAuthenticationData.question, then get hidden (*) input invisible to the user, i.e. a password, and proceed to the next operation in the list.
- bDirAuthenticationOperationAuthenticate
- tells Director to finish all user interaction and asks plugin for authentication using bDirEventAuthenticate plugin event.
Every authentication operation of bDirAuthenticationOperationPlain and bDirAuthenticationOperationHidden will return with an user response data which will be forwarded directly to plugin using bDirEventAuthenticationResponse plugin event. No other operations will do that. During this event a plugin is responsible to save user response as it won't be saved by Director and lost forever. These collected responses should be used for final user authenticate. The response is passed to plugin with bDirAuthValue.response variable and filled with seqdata value from current question operation.
As soon as the number of questions (authenticate operations) defined during registration (the bDirAuthenticationRegister.num value) comes to the end or one of the operation executed is bDirAuthenticationOperationAuthenticate then Director will stop asking a user more questions and will generate the bDirEventAuthenticate plugin event. During this event handling a plugin is responsible to verify all responses and perform user authentication.
There is a special operation in BPAM: bDirAuthenticationOperationPluginAll which tells Director to asks in runtime the plugin for every single operation to execute. This allow to build a dynamic authentication procedure with a variable number of questions and challenges. In this case a plugin is responsible to explicitly finish a workflow with bDirAuthenticationOperationAuthenticate.
You can find below some examples for above structures.
static bDirAuthenticationData testquestions0[] =
{
// operation; question; data;
{bDirAuthenticationOperationLogin, "Username:", 0},
{bDirAuthenticationOperationPassword, "Password:", 1},
};
static bDirAuthenticationRegister testregister0 =
{
.name = "PLUGIN_NAME",
.welcome = "This is a test authplugin API Plugin. Use root/root to login.",
.num = 2,
.data = testquestions0,
.nsTTL = 0,
};
Above you can find a simplest user/password authentication scheme with plain (visible) user input and hidden (invisible) password input.
static bDirAuthenticationData testquestions1[] =
{
// operation; question; data;
{bDirAuthenticationOperationLogin, "Username:", 0},
{bDirAuthenticationOperationPlugin, NULL, 1},
{bDirAuthenticationOperationPlain, "Response:", 2},
};
static bDirAuthenticationData testquestions1_msg =
{
// operation; question; data;
bDirAuthenticationOperationMessage, NULL, 0
};
static bDirAuthenticationRegister testregister1 =
{
.name = "PLUGIN_NAME",
.welcome = "This is a test authplugin API Plugin. Use bacula username to login.",
.num = 3,
.data = testquestions1,
.nsTTL = 0,
};
Above you can find a simplest MFA (challenge-response) authentication scheme with out of band authentication verification. In this example a plugin will display a message prepared in runtime by plugin.